The Hunt for the Best Gigabit Home Network VPN

A common suggestion I make to people who are looking to improve their online privacy is to use a VPN. There are a variety of reasons you may want the protection of a VPN; my primary concern is to avoid leaking the true IP address of my home which could be used to probe my network for vulnerabilities and also to get a rough geolocation on me.

For convenience, I recommend setting up a VPN client at your home router so that all of your devices are automatically protected and you don't have to configure every device separately. However, running your VPN client on the router does has a major downside: performance.
It really sucks to pay for gigabit internet but be throttled below 10 megabits due to OpenVPN protocol overhead. Looks like WireGuard should provide between 10X and 50X improvement on routers; hopefully more VPNs and routers will add support for it in the coming years.
— Jameson Lopp (@lopp) October 5, 2020
Unfortunately, OpenVPN, which is one of the most popular and widely supported VPN protocols, requires a decent amount of computational power to run at high throughput. It's also a single-threaded protocol, so you can't take advantage of CPUs that have multiple cores.
Enter Wireguard. It's a fairly young tunnel (few years old) protocol that promises far greater performance, though it's still not supported by many VPN providers or router software. Wireguard support was added to the Linux kernel in March 2020, making it easy for Linux users to install. You can learn more about Wireguard pros and cons here.
VPN Performance
Below are some comparisons of throughput performance for different CPU architectures. The CPU tends to be the bottleneck on devices because running a VPN client requires constantly encrypting and decrypting data as it is sent and received by the device.
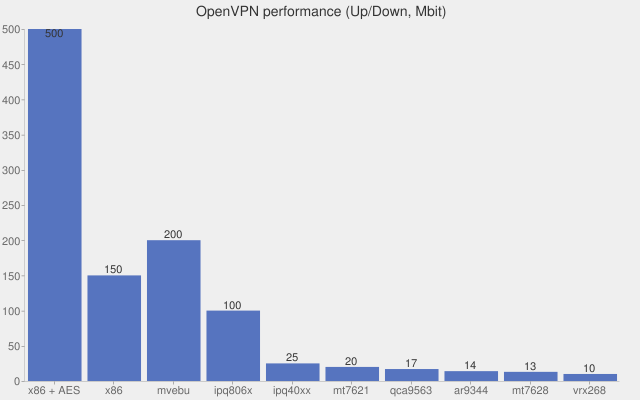
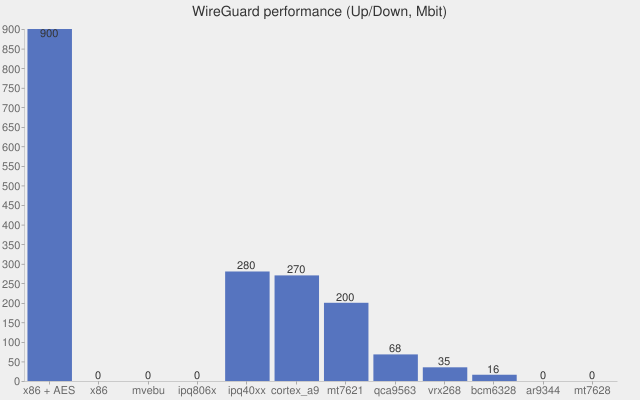
These charts can be tricky to grasp without cross referencing this hardware table.
But in general:
- x86 - general CPU architecture, this is the performance you should expect if you are running the VPN client directly on a laptop/desktop.
- mvebu - Linksys WRT routers
- ipq806x - Netgear R7*** routers
- ipq40xx - Misc Asus / Linksys / Netgear / other routers
- bcm53xx - Asus RT-AC**U routers
From these charts it appears that Wireguard can improve throughput on low powered CPUs by 10X in comparison to OpenVPN if you're using a Linux kernel that supports it.
It's unfortunate that the Asus performance is on the low end of the spectrum; I run some of my routers with DD-WRT and some with AsusWRT-Merlin firmware and highly prefer the UX and configurability of the latter.
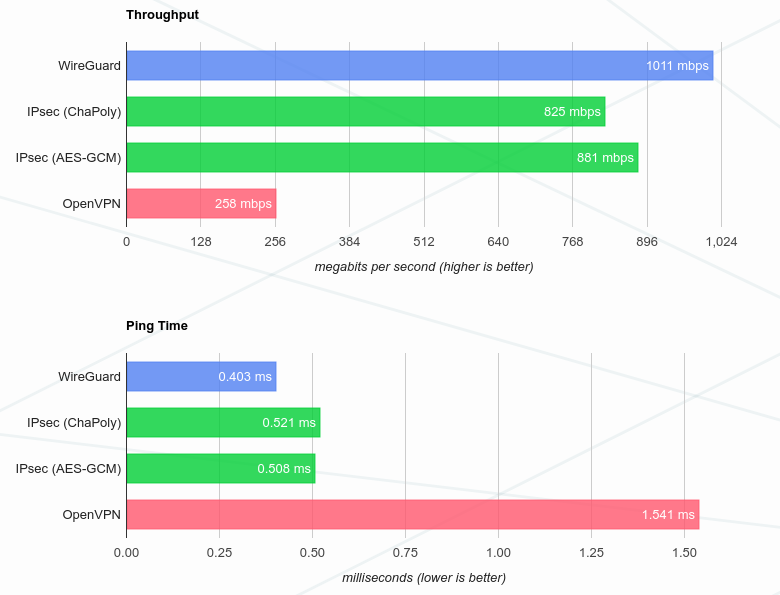
Wireguard has their own performance benchmarks on an (x86) Intel Core i7:
Before I dove too deep, I ran a quick test on my Android phone. First I ran the speed test while using an OpenVPN tunnel that is configured on a ASUS RT-AC88U router. Then I installed Mullvad's Android app and used a tunnel that connected to a server in the same city as my OpenVPN tunnel. The results were impressive: 9X faster on my phone.
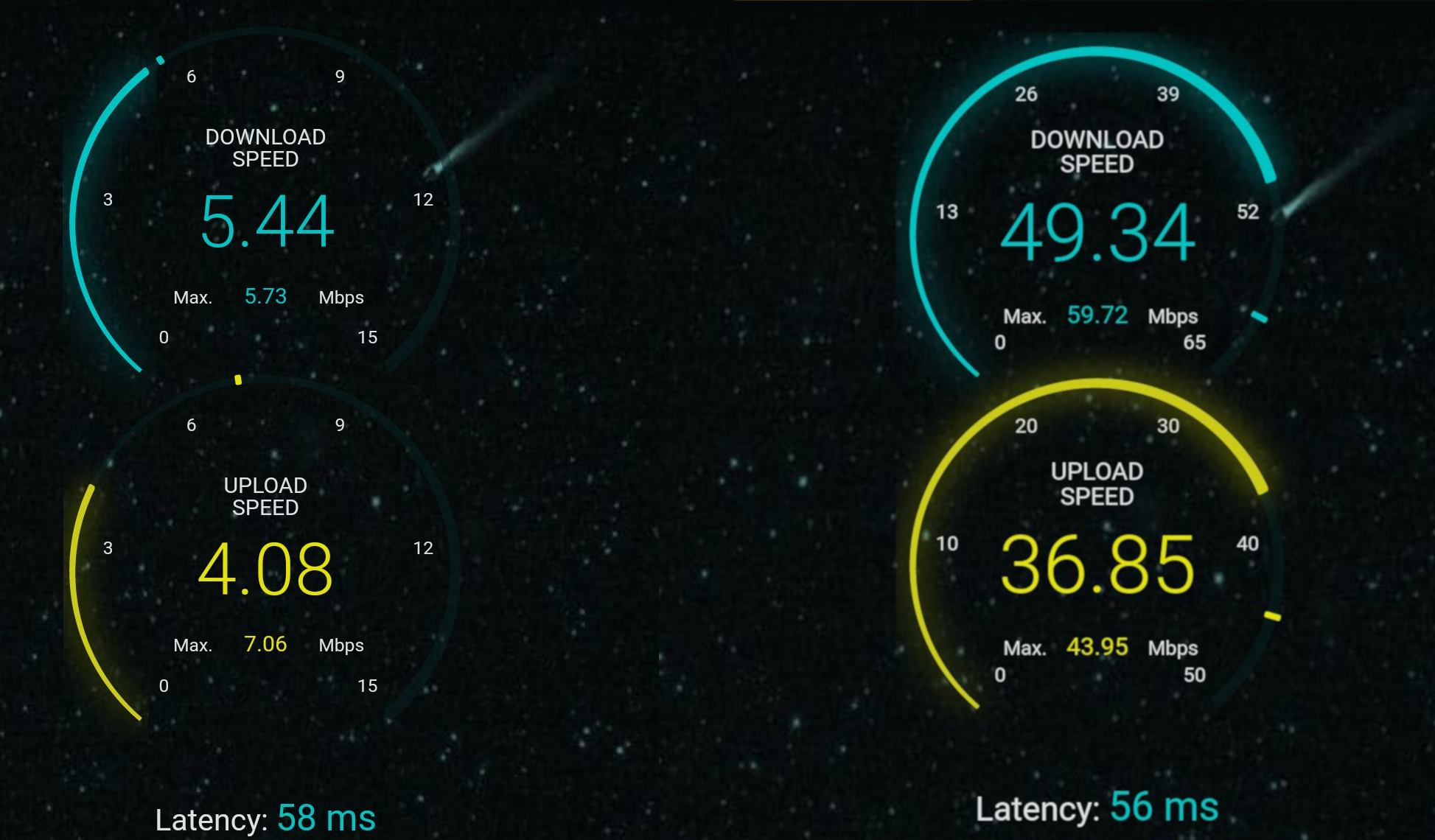
50 Mbps is great, though it's still only 5% of the bandwidth for which I'm paying my ISP. I'd like to do better!
I also have a Linksys WRT3200ACM running DD-WRT that is configured as an OpenVPN client. I decided to run a comparison test to see how its performance fares. We can see the download speed is 11X faster compared to the ASUS router, which is in line with expectations due to the CPU architecture differences. Note that in this test the upstream is limited by the ISP rather than the router.
Common Wireguard Architecture
There are plenty of guides floating around such as this one and this one that describe how you can create a server somewhere in a data center that runs wireguard and you can configure all of your devices to send their traffic through a wireguard tunnel to it, where it will then relay the traffic out to the broader internet.
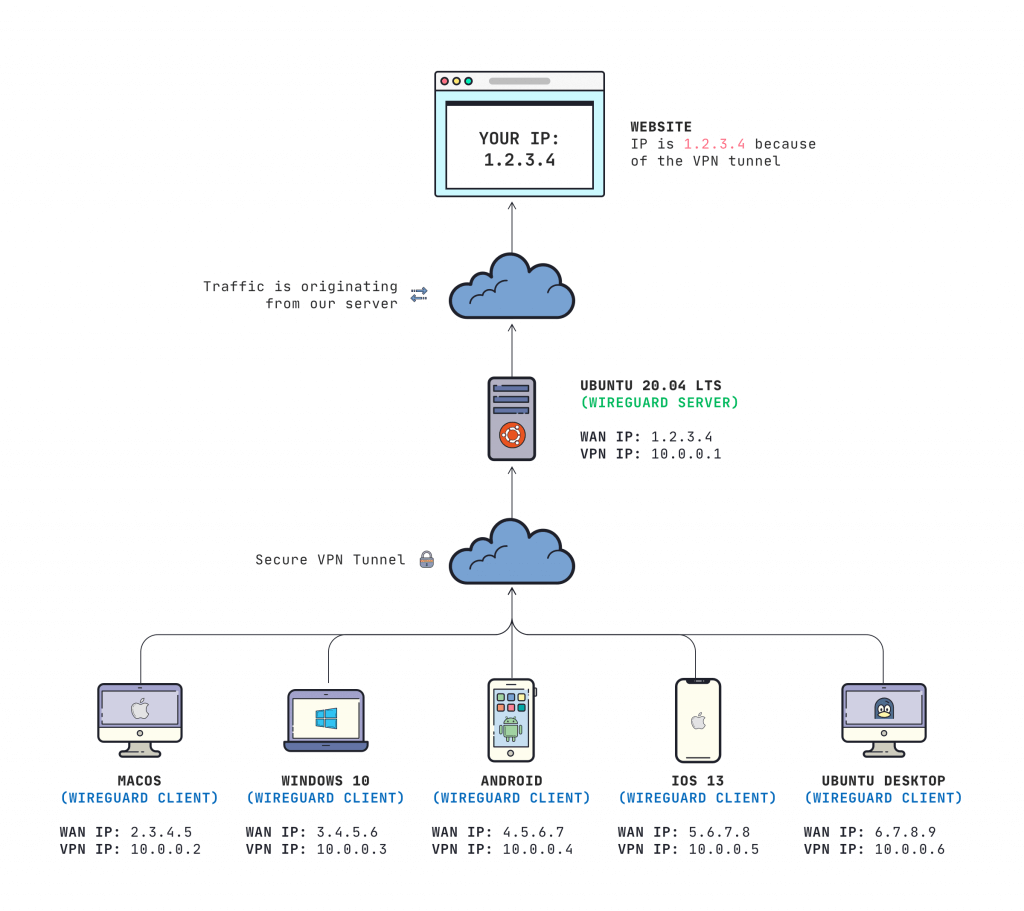
However, I consider this to be a huge pain because you end up having to configure N + 1 devices - all of the devices in your home network + your VPN server.
A Simpler Setup
For user friendliness my ideal scenario would be what I've been doing for years: a single hardware device that acts both as my Wi-fi router and as a VPN client with simple UX for managing which traffic from which devices goes through the tunnel. The network architecture should look like this:
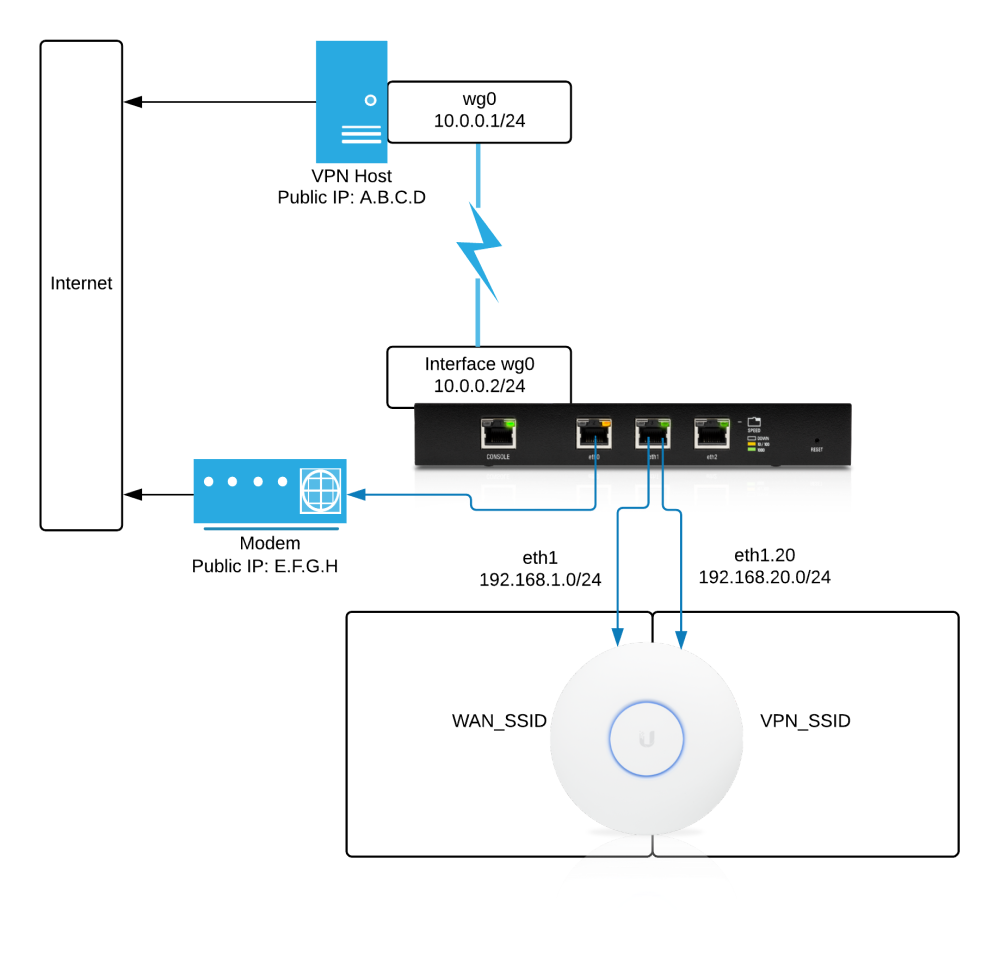
Why is the latter point important? You probably have some services you use that will block traffic from commercial VPNs. A few years ago I wrote a guide for how to configure DD-WRT to support policy-based routing:

But it's pretty clear that an all-in-one device is not going to happen. During my research I actually came across an excellent post that I wish I had bookmarked. The gist was that you're never going to get the best of all worlds by restricting yourself to a single device that tries to do everything. Rather, by using specific devices for each task and connecting them to act as a single logical device, you'll have greater flexibility and performance at the cost of increased complexity and thus worse user experience on the setup and maintenance side.
Current WireGuard Options
It is possible to set up a WireGuard client on a router running DD-WRT. I'm not a fan of DD-WRT because I prefer ASUSWRT's routing policy GUI. Also note that unless you install DD-WRT on a device with an x86 CPU architecture (a laptop / desktop / mini PC) you'll still be limited to under 300 megabits per second.
Running on (only specific newer) ASUS hardware is still very experimental. From what I can tell it requires a decent amount of scripting and is pretty challenging to set up. And if you are successful, the CPU on the router will still limit you to a few hundred megabits per second.
Running a WireGuard client on older ASUS hardware is even more complicated to try to get running.
You can run a WireGuard server on a Raspberry Pi but that's not going to help you route your home network traffic through the tunnel - it's for making it easy for you to reach your home network securely when you're not at home.
You can run WireGuard on Ubiquiti router with this firmware, though this doesn't seem to be something that's officially supported by Ubiquiti. There's a decent how-to guide here, though I've been unable to find any hard performance numbers. According to this post, MIPS CPUs perform worse than ARM... and Ubiquiti EdgerRouters have MIPS64 CPUs, which would mean that a Raspberry Pi would outperform an EdgeRouter.
GL.iNet GL-MV1000W (Brume-W) supports WireGuard but doesn't have great reviews as a general Wi-Fi router.
PfSense added WireGuard support a year ago and OPNsense has a wireguard plugin as well. I did some research into these two projects and found that they are both forks of an earlier project and it sounds like OPNsense is a more actively developed project with a better interface.

It also looks like some folks rig a setup with wireguard tools or this guide and then configure their router to send all outbound traffic to the machine running the wireguard client.
In general the last 3 options appear to be most promising in terms of performance because you should be able to run them on machines with x86 CPUs.
Plug & Play VPN Hardware
Shellfire supports WireGuard but for some reason is limited to 50 Mb/S and is not a sufficient improvement to interest me.

Vilfo is an OpenVPN router but looks like an Intel NUC; doesn't seem worth $380.

There are a ton of "VPN Routers" being sold that are little more than popular router hardware that has custom firmware loaded onto it along with a preconfigured VPN. Beware that these are overpriced and you're essentially paying hundreds of dollars extra for the convenience of saving a few minutes setting up the software. For example, I myself have used an Asus AC3100 for several years. It retails for $250 but this service sells a preconfigured one for $400.

This Uban VPN Box looks very user friendly. It's ARM-based, but uses OpenVPN so I'm sure the performance will be bottlenecked and thus won't be able to make use of a full gigabit connection.
Winston looks like the perfect UX for a VPN device. No configuration necessary; you just plug it between your modem and router and it does the rest. It even supports up to 500 Mbps throughput. However, it looks like the device is only designed to protect web browsing, not all internet activity.
Winston only routes "Clearnet" (port 80/443) activity over the privacy mesh network. Protocols widely used to hide illegal activity like BitTorrent and Onion are not supported.

Syfer also looks like the perfect UX for a VPN device. No configuration necessary; you just plug it between your modem and router and it does the rest. It's a shame that the VPN speeds are limited to 100 Mbps, otherwise I'd have tested it out. Looks like they went out of business between the time I started researching and when I published this article.
Finally, after over a year of keeping my eye out for VPN hardware products I recently ran across ProtectLi. This looks like it checks all the boxes:
- Dedicated small form factor hardware
- x86 CPU (up to quad core)
- Supports both pfSense and OPNSense, which have WireGuard support.
The Journey Has Just Begun
It was overwhelming to see how many different options there were for implementing WireGuard and how few of them seem to be officially supported by hardware and software providers.
Now that I've finally settled upon a path for implementation, I expect to spend several months testing the setup, maintainability, and overall reliability of ProtectLi + OPNsense + WireGuard. Stay tuned for my follow-up guide and review!
If you're aware of any other good options that I've missed, please let me know.








