Casa's Privacy Model
A transparent explanation of our privacy practices, and how you can increase the privacy of your personal information.
Satoshi Roundtable IV Recap
It was my pleasure to once again attend the Satoshi Roundtable; this year it was scaled up immensely and I didn’t even have a chance to…
The Challenges of Building Ethereum Infrastructure
Several of our engineers, myself included, have spent a substantial portion of the past year working on building low level Ethereum…
What the Data Tells Us About Bitcoin in 2017
A variety of metrics show that Bitcoin is at the forefront of an increasingly complex ecosystem that continues to grow in many ways.
Securing Your Financial Sovereignty
How and why to defend your bitcoin with a full node.
Could SPV Support a Billion Bitcoin Users? Sizing up a Scaling Claim
A deep dive into what would be required to scale Bitcoin via simplified payment verification.
Bitcoin and the Benefits of Coopetition
Lopp makes an impassioned argument for the need for more cooperation between the players in the bitcoin space.
The Challenges of Bitcoin Transaction Fee Estimation
Making predictions is hard, especially when they're about the future!
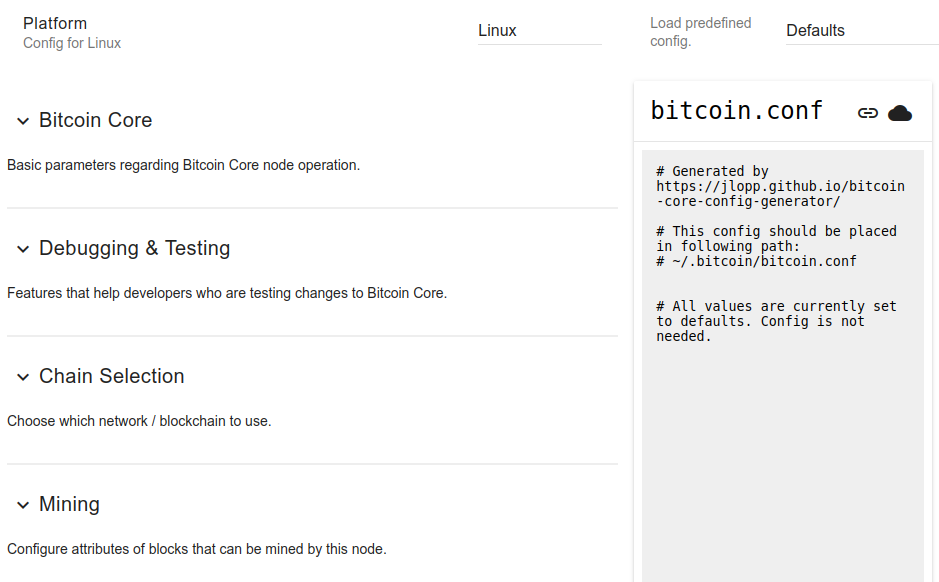
Announcing the Bitcoin Core Config Generator
Bitcoin Core is a complex piece of software. Because one of the primary goals of Bitcoin is to enable users to be self sovereign and have…
Nobody Understands Bitcoin (And That’s OK)
No one has found the bottom of the Bitcoin rabbit hole.