It's Knot a Serious Project
A comprehensive compilation of controversial actions and statements by Luke Dashjr.
Bitcoin Address Poisoning Attacks
An investigation into likely address poisoning attacks occurring on the bitcoin blockchain.
How to Securely Create a Bitcoin Seed Phrase in 9 Simple Steps
A user-friendly guide for how to generate seed phrases from your own entropy.
How Many Bitcoin Confirmations is Enough?
How safe is it to accept a bitcoin transaction after X confirmations? A deep dive into the math behind quantifying double-spend risk.
Crypto's Kryptonite: Complexity
Thoughts on navigating the wider crypto ecosystem and evaluating risks of new projects.
Are Chinese Miners a Threat to Bitcoin?
Is the concentration of hashpower within the borders of China a cause for concern about a nation state attack against the network?
Firearms for Home Defense
Considerations to take regarding firearm selection, training, and storage for home defense.
How to Securely Back Up Data to Cloud Storage
Jameson researches user-friendly solutions for backing up sensitive data to cloud providers while keeping it safe from third party snooping.
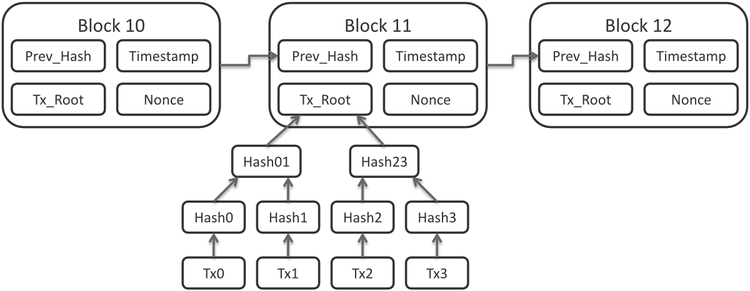
Bitcoin Timestamp Security
A deep dive into the game theory behind keeping timestamps of bitcoin blocks reasonably accurate.
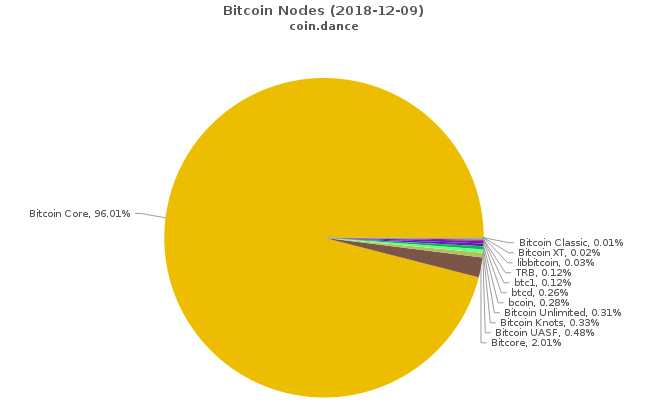
Who Controls Bitcoin Core?
Understanding how the focal point of Bitcoin development operates.