A Critique of Softwar Concepts

Major Jason Lowery caused quite a stir in August of 2021 when he published a post on LinkedIn claiming that Bitcoin was violence. It certainly rubbed a lot of folks the wrong way, and it earned him a large following shortly thereafter when he joined Twitter.
I hadn't paid much attention to the drama or his claims until recently when more people started asking for my opinion, likely because he has honed the thesis for the past 2 years, has hit the podcast circuit, and recently published his thesis as a book.
To be clear, I have not read the 350 page book that is for sale on Amazon. I find it odd that, given this is an academic thesis, I'm unable to find a PDF of it available anywhere. According to MIT's Thesis Library, theses are received one month after degrees are granted - so it may not be available until July or August. To my knowledge, there's nothing preventing Lowery from self-publishing his thesis right now; apparently he wants the downloads to be tracked through MIT and he wants to have a more impressive metric of being a best selling book on Amazon. Paying $40 for the privilege of receiving the thesis leaves a bad taste in my mouth, as rational discourse should occur in the public domain rather than behind a paywall. As such, the following essay is a result of the notes I took from listening to 10+ hours of Lowery explaining his thesis in a variety of venues. The links to those videos are provided near the end of this essay.
Update: Lowery finally posted a URL to the thesis PDF in response to this essay. I reviewed the thesis in greater detail in the following post:

Hopefully Lowery and his adherents do not resort to retorting that my points are invalid because I haven’t read the book. That’s not how one engages in rational discourse - saying “you can’t criticize me without buying my book” is just a disingenuous marketing tactic. Anyone who employs that deflection on me will be written off as bad-faith actor. I invite those who disagree with this essay to raise specific counterpoints rather than attempting to hand-wave away my criticisms.
TL;DR: Lowery is an intelligent fellow who has crafted a compelling story. I agree with the vast majority of his premises, and I suspect that this is why so many people have bought into the narrative. But the devil is in the details, and in this critique I'll point out several flaws and unanswered questions that leave me unconvinced of his conclusions.
A Critique of Criticism
I have surveyed the landscape of those who have criticized Lowery and found it lacking.
Many folks out there are slinging ad hominem attacks at him due to his military background. Lowery surely loves to see these fallacies coming his way, as it makes his critics look like fools. Everyone is free to contribute their ideas to Bitcoin; it is, in fact, a free market battleground of ideas. Rejecting someone's ideas because of their background is ridiculous.
Similarly, many folks are making emotional arguments about Lowery's characterization of terms like "violence / weapon / force." Once again, this is not the appropriate target to attack with regard to his arguments.
One notable exception is Limpwar, though it’s more of a standalone thesis than what I'll attempt in this essay - a more concise focus on pointing out flaws and logical errors.
The Good
Lowery does a good job setting the historical stage. Nature is not friendly to life; all life competes over the scarce resources necessary to survive and thrive. Evolutionary arms races occur organically between predators and prey.
The US military has expanded its domains over time via the Army, Navy, Air Force, and Space Force. Lowery makes a good point that every form of territory becomes a battleground and he calls cyberspace the "fifth domain" of warfare.
A lot of folks seem to be upset because Lowery describes the natural state of competition over scarce resources as warfare. My perspective is that his main point is that all of nature exists in a state of anarchy. Nation states also exist in a state of anarchy with each other, and military thinking takes this into account.
Bitcoin is crypto anarchy - each node operator chooses the rules to which they agree. Consensus emerges out of chaos; no one has the power to force you into consensus against your will. Beware of those who attempt to convince you that a formalized governance structure exists.
— Jameson Lopp (@lopp) January 15, 2018
Thus, I can see an overlap in terms in the sense that anarchy (systems without rulers) are automatically in a state of perpetual conflict that you could characterize as "warfare." He’s just using terms differently than from what many of us are used to, but from a military perspective they are accurate. This shouldn't be surprising, because as the old saying goes:
"When all you have is a military, everything looks like a war."
The Bad
Lowery says that currently people attempt to secure data via "some magical combination of logic" and "if-then-else statements" that are coded into software. Well, kind of, but there are a variety of authentication mechanisms that are "encoded logic." There's far more to it than just logic. This point strikes me as cherry picking and a mischaracterization.
"No amount of logic can protect you from the systemic exploitation of logic."
Technically correct, but this sounds like a strawman argument because cybersecurity is more than just pure logic. I get the general feeling that his depth of knowledge when it comes to cybersecurity is rather shallow. For example, his mispronunciation of sybil attack as "psybill." This suggests to me that he has never spoken with anyone about sybil attacks, nor seen any presentations about them - he has only read about them. Of course, this tidbit is not an argument in and of itself - it’s merely an observation that may help explain why Lowery has made several omissions.
He keeps talking about securing data but I've only actually heard him talk about DoS prevention. Not so much securing data in terms of its integrity. On his most recent interview with Robert Breedlove, Lowery states:
Cybersecurity will have a physical component to it, we're just waiting for that thing.
Yes, cybersecurity does have physical components. No, we're not waiting on them. Allow me to introduce the 3 forms of human authentication:
- Something you know (such as a password)
- Something you have (such as a smart card)
- Something you are (such as a fingerprint or other biometric method)
Note that 2 of the 3 forms of authentication are physical in nature. Though biometrics is arguably a weak single factor of authentication for several reasons I won't get into.
Lowery also makes what I consider to be a pretty weak argument that Bitcoin is defensible via Second Amendment constitutional claims. I'm not a lawyer, but Second Amendment claims have been shot down time and time again - the Supreme Court has clearly stated that there are restrictions. For example, the ownership of fully automatic firearms, explosives, artillery, laser guided missiles, etc, are all not a right under the Second Amendment. When a new innovation appears, such as the bump stock, the BATFE often moves to ban it, and all owners of such devices are required to turn them in or face imprisonment. The Second Amendment only permits Americans to own a very small subset of the weapons available on the market; its "protections" are relatively weak and fickle - it's not something I'd want to rely upon.
First Amendment claims, on the other hand, are far more powerful.
Let us not forget the lessons of the 1990s era Crypto Wars. Strong cryptography was literally classified as a munition (weapon.) How did the Cypherpunks win their legal battles? It was NOT by making Second Amendment claims, but rather via First Amendment claims.

Lowery even goes so far as to make a counterpoint about Zimmerman's PGP export case not setting a precedent for a First Amendment defense. That claim is correct... but he's cherry-picking again. What Lowery doesn't mention is Bernstein v. USDOJ. The Ninth Circuit Court of Appeals ruled that software source code was speech protected by the First Amendment and that the government's regulations preventing its publication were unconstitutional.
I reject Lowery's framing that the legal arguments in the 1990s were made with the Second Amendment in mind. Rather, the claims were that weak encryption was harming the safety and limiting sales and growth of e-commerce. This led to a series of relaxations in US export controls, culminating in 1996 with President Bill Clinton signing Executive order 13026, transferring commercial encryption from the Munition List to the Commerce Control List.
The Unsaid
I've yet to hear a proposal of how Lowery’s perspective will lead to new solutions. In general the theory feels quite lacking in terms of practical applications. Lowery speaks very broadly as if this will secure all data in the world, but I don't see the connection. Here's a good summary of Lowery's claim:
For those certain control actions that you don't want to be exploited, like the ability to write the ledger, for example, or the ability to spam you, you want that to be physically constrained.
This claim is compelling because it does describe one facet of how Bitcoin works. But the point of honing and publishing a thesis is to advance an original point of view as a result of research. I have yet to see any examples of Lowery showing how his thesis can be applied to secure non-Bitcoin data.

It's hard for me to imagine a government mining operation operating anywhere near the efficiency of privately funded operations; the profit motivations simply aren't there. Lowery insists that "data defense" motivations exist, but as mentioned, that's a completely missing link in his arguments. He also claims that since the military has a mission to protect the ability of citizens to access economic thoroughfares, this will naturally extend to Bitcoin.
I pose to you that, should Lowery's claims be accepted and adopted by the American military, the "cure" could be worse than the disease. Let's approach Lowery's proposed future adversarially. In a worst case scenario, government miners could operate at a huge (taxpayer-funded) loss and effectively bankrupt privately funded miners all around the world. The only way a nation state can ensure that blockchain data is not censored or overwritten is to control a majority of the network hashrate. But, by doing so, they would be destroying one of Bitcoin's major strengths of its game theory - that hashpower is distributed sufficiently and incentives are aligned such that no entity has a majority of the network hashrate.
One major missing link is that hashing power is not the only mechanism that secures the bitcoin blockchain. There are already many rules and non-mining entities that vastly restrict the data in the blockchain. The hashpower only defends the integrity of said data from a historical perspective.
By focusing on hashpower, he implies that thermodynamic security is the fundamental aspect of the Bitcoin network's security model. This is incorrect and lacks nuance. There are lower levels of Bitcoin's security: the nodes that form the peer-to-peer network and the humans who collectively organize to agree upon what code they will run to secure the network.
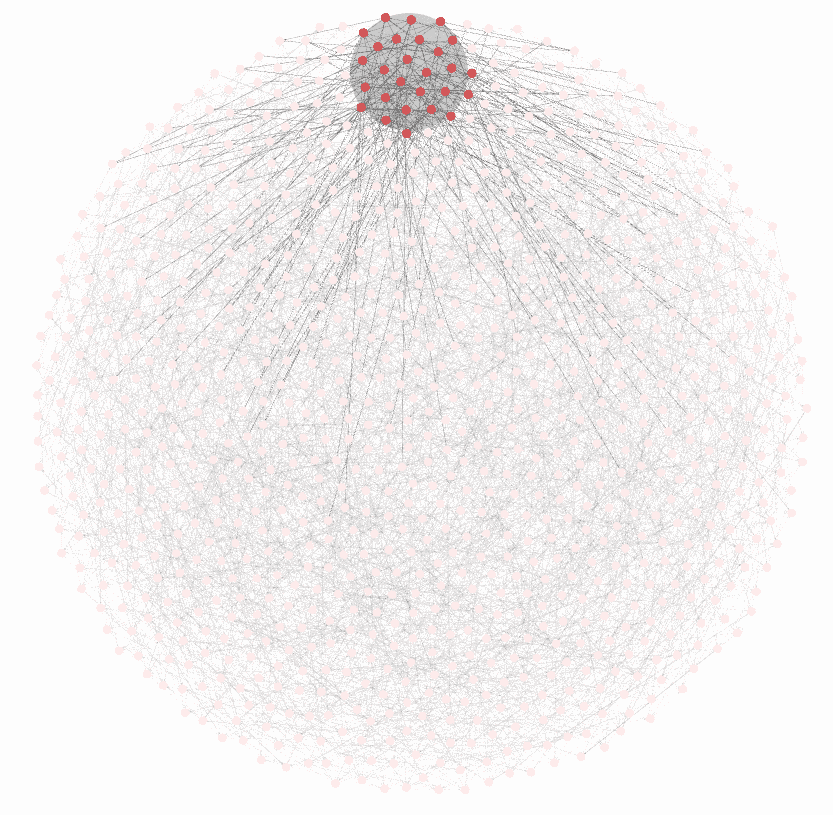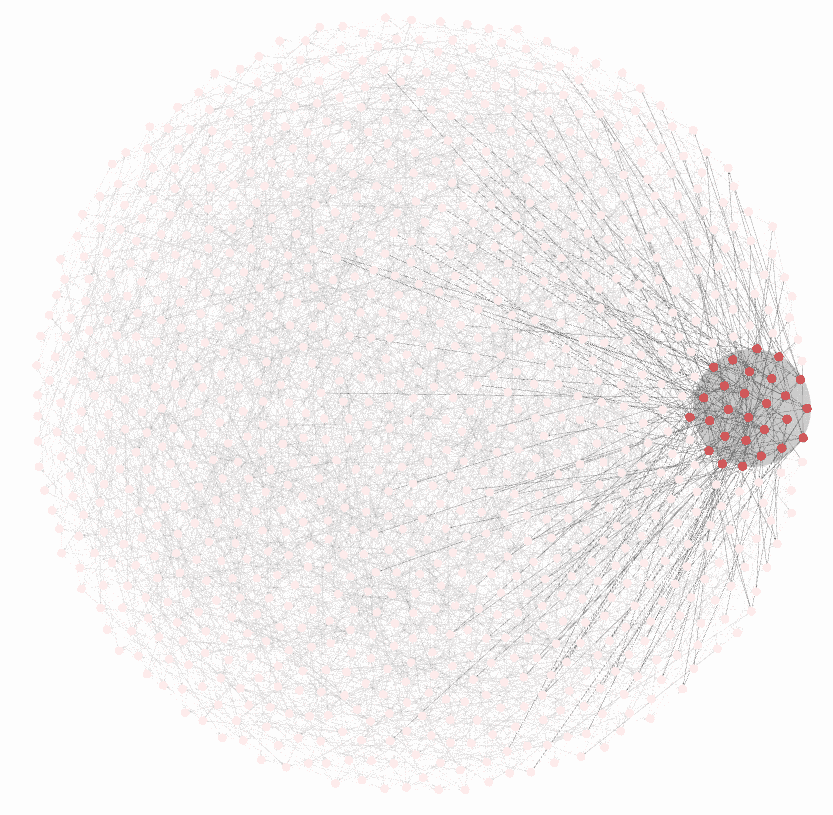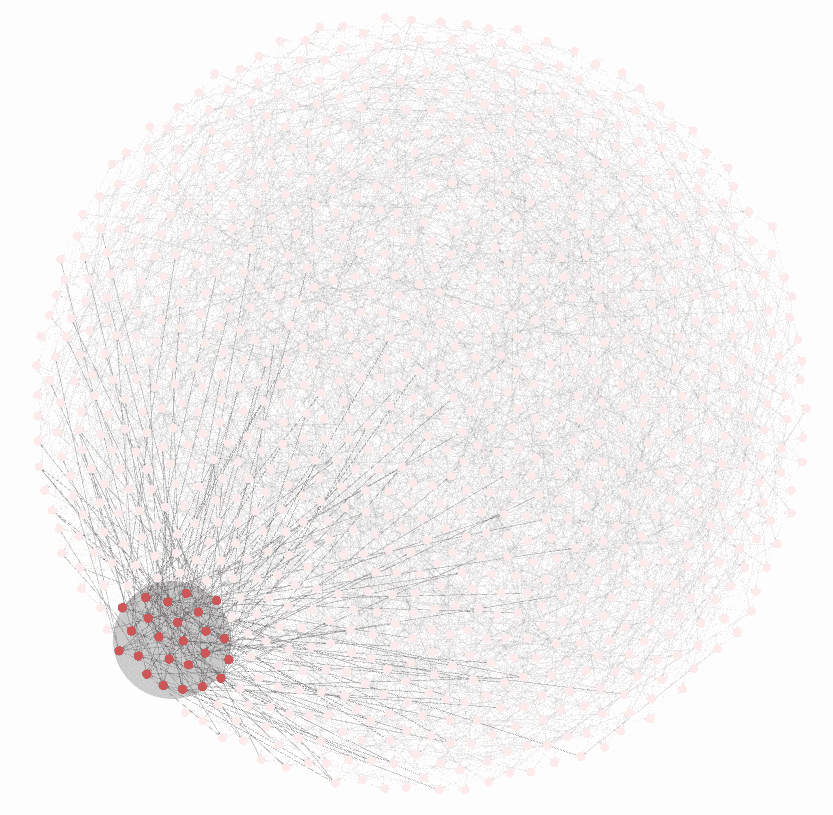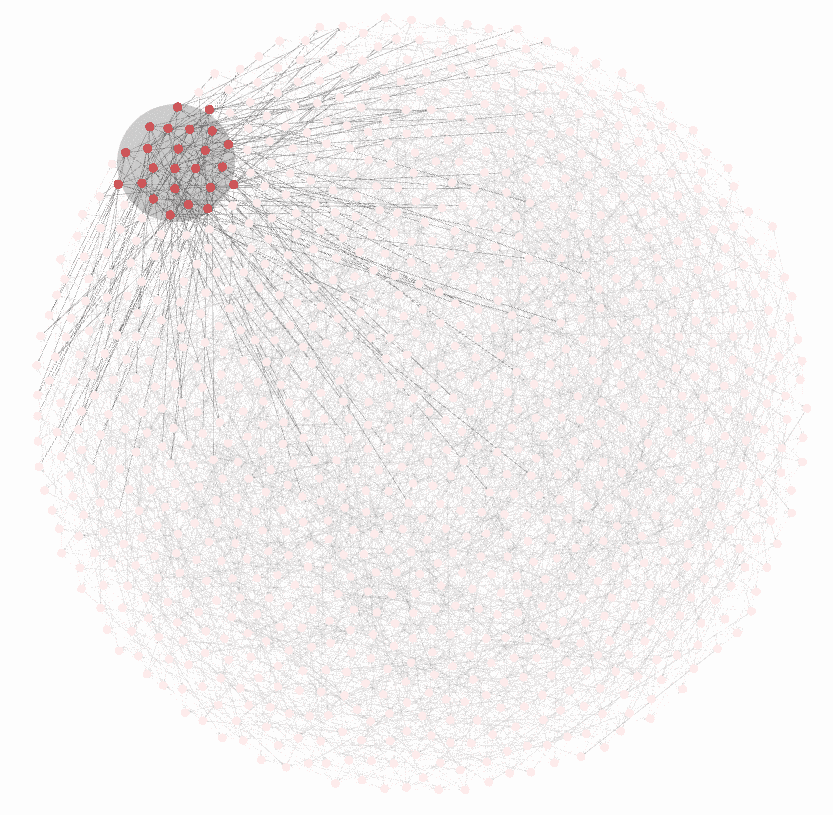
This is why Bitcoin is fundamentally not protected by electricity, hashing machines, or even the "logical security" of nodes. Bitcoin is backed by a volunteer militia. The antifragile nature of Bitcoin as an ecosystem is because it's an open source project without a central coordinator.
Nakamoto consensus is a proxy for meatspace consensus. If something's wrong, we fall back to meatspace consensus, patch code, and carry on.
— Jameson Lopp (@lopp) December 6, 2015
Concerningly, Lowery glosses over an entire industry that already exists.
"We've never had this fifth domain through which you could fight wars."
Surely he has heard of United States Cyber Command?
USCYBERCOM plans, coordinates, integrates, synchronizes and conducts activities to: direct the operations and defense of specified Department of Defense information networks and; prepare to, and when directed, conduct full spectrum military cyberspace operations in order to enable actions in all domains, ensure US/Allied freedom of action in cyberspace and deny the same to our adversaries.
This claim is particularly absurd; cyberwarfare is already a thing. Nation states (and independent black hats) probe the defenses of critical infrastructure on a daily basis. The fact that warfare can be conducted via internet protocols does not magically remove the physical attributes and consequences of cyberattacks. For example:
- In 2021 the Darkside hacking group managed to shut down the Colonial Pipeline - 45% of America's east coast fuel supply - for several days.
- In 2021 a hacker managed to increase the amount of sodium hydroxide, a corrosive chemical, by 100X in a small Florda town's water supply.
- Russian-backed hackers remotely disabled electricity to a wide swath of Ukraine in December 2015. Then they uploaded faulty firmware to make fixing the breach even more difficult.
- In 2014, hackers caused massive damage to a German steel mill by causing them to lose control of a blast furnace.
- From 2007 to 2010 the US physically destroyed Iran's centrifuges that they used to enrich uranium for their nuclear program with a virus called Stuxnet.
- In 2008 a teenager from Lodz, Poland tripped rail switches and redirected trams using a homemade transmitter. His stunt injured twelve people when four trams derailed.
- An Australian man was convicted of hacking into his small town’s computerized waste management system in 2001 and deliberately spilling 265,000 gallons of raw sewage into parks and rivers in the area.
If nation states started running large mining operations, they wouldn't be able to harden that infrastructure in the same way that military / government / utility infrastructure is hardened by partitioning it from the Internet. This infrastructure will have a physical presence and it will necessarily have both physical and digital weaknesses due to the nature of its position in both meatspace and cyberspace. It requires some magical thinking to believe that we can invent a new form of cyberwar devoid of physical consequences.
Cyberspace is an extension (or layer on top) of meatspace, not a completely parallel universe. Just as how Neo could act like a god with little consequences while in the Matrix, if the Sentinels found him in meatspace, it was game over.
KISS (Keep it Simple, Stupid!)
If you can't explain it simply, you don't understand it well enough.
- Variant of a quote by Lord Rutherford of Nelson
Lowery's interview with Peter McCormack was 2.5 hours.
His latest interview with Robert Breedlove was 2.5 hours.
His interview with Marty Bent was 3.5 hours.
There's a whole other 6 hours of What is Money mini-series featuring Lowery.
His book is 350 pages; one Amazon reviewer notes that it doesn't start talking about Bitcoin until page 230.
What if Lowery's thesis itself is a denial of service attack? It was incredibly time consuming for me to find the flaws in his narrative because they are the proverbial needles in the haystack, and the biggest flaws are not in what he says but in what he doesn't say.
So What?
Lowery's presentations are compelling because he accurately portrays (one mechanism of) how Bitcoin defends itself without a central controller. But it falls short on how this applies more broadly to other systems.
Lowery keeps talking about us needing a way to protect our data in cyberspace. After watching 10 hours of him talking, I have yet to see him propose a single practical example of how he envisions accomplishing that. McCormack pushed him for examples but the only one he could come up with was the data in the Bitcoin blockchain itself.
It's such an odd claim that I'll quote Satoshi Nakamoto in response:
Before strong encryption, users had to rely on password protection to secure their files, placing trust in the system administrator to keep their information private. Privacy could always be overridden by the admin based on his judgment call weighing the principle of privacy against other concerns, or at the behest of his superiors. Then strong encryption became available to the masses, and trust was no longer required. Data could be secured in a way that was physically impossible for others to access, no matter for what reason, no matter how good the excuse, no matter what.
Lowery again, in his recent Breedlove interview:
If you create a new domain that has no mass, which is what cyberspace is, then how do you project power through that domain? If it's got no mass then you can't project power or impose physically prohibitive costs using mass-based power projection technology, so kinetic power projection is out the window. You're not using force to displace mass... it has to be, probably, some type of electromagnetic thing like electricity.
Encryption fundamentally imposes physically prohibitive costs upon attackers. By design, it creates an amazing asymmetric defense capability - that is, it costs practically nothing to encrypt data while decryption costs many orders of magnitude more computational resources - in many cases, more resources than can even be harnessed by our current level of civilization. Lowery may dismiss this point by claiming that encryption is only "using logic," but this is just an issue of private key management. It is quite practical to pull key management security out of the digital realm and into the physical realm via dedicated airgapped hardware.
I'm disappointed because I've yet to see Lowery discuss game theory at the nation state level of mining bitcoin in depth. In this interview he does seem to imply that the Federal Reserve and US Treasury will fail to remain competitive in a world of hyperbitcoinization - that other nation states adopting Bitcoin could result in them destroying the US' monopolization on being the world reserve currency and defender of property rights via projection of power. But in that video he only seems to talk about the Federal government acquiring bitcoin, not mining it as a security play for the integrity of data.
If one of his arguments is that "the US should hedge against the possibility of hyperbitcoinization in order to survive" - I can accept that claim, at least in the scope of money.
But Lowery claims that Bitcoin creates a replacement for the kinetic power projection game and is a threat to the United States' "business model" of exporting property defense across that world. That's some massive hand-waving and I fail to see how the dots get connected between Bitcoin and everything else - there are many other forms of scarce resources than just BTC that we should expect nation states to continue to wage kinetic war over. As noted previously, cyberspace and meatspace are inextricably linked and his vision of non-lethal warfare strikes me as utopistic.
Conclusion
Lowery is a gifted storyteller. He makes logical arguments for why Bitcoin is a better form of money with which governments and central banks won't be able to compete.
It's impressive that he has crafted a narrative that may have a strong chance of getting various government agencies to look more favorably upon Bitcoin. However, and this is crucial: Lowery's focus on Proof of Work is severely lacking because Proof of Work is but ONE of many aspects of Bitcoin's game theory and security model.
I agree with his claims:
- about evolution of systems and power dynamics
- that governments should hold bitcoin as a hedge
I'm skeptical of his claims:
- that governments will be incentivized to mine bitcoin
- that it's desirable for governments to participate in bitcoin mining
I disagree with his claims:
- about cybersecurity
- about the second amendment
- about general data integrity assurances
- that PoW creates a new domain of non-lethal warfare
- that cyberspace warfare will displace kinetic warfare
I like the story arc. I don't buy the conclusion. In fact, the entire thing appears to be a giant non sequitur. That is to say: just because you string together a huge number of valid premises, that does not mean that your inferences are logical.
Perhaps it doesn't matter what I think; I'm not the target audience. However, it is worth considering the implications of what might happen if his target audience accepts and adopts this thesis.