Softwar Thesis Review

Last week I published a critique of several high level claims and concepts that have been made by Major Jason Lowery on a variety of venues such as conferences and podcasts. Predictably, this ruffled some feathers.

Also, predictably (as I had already countered in the above essay) nearly all of the rebuttals I received to my questions were that I hadn't read the full thesis. I don't find such arguments to be made in good faith, as they are a verbosity fallacy that forces the critic to prove a negative by committing a great deal of resources.
Exclaiming "read my 400 page thesis" is not a fair rebuttal to specific criticism. If anything, it's an asymmetric denial of service attack designed to shut down the critic. A thesis author ought to be able to point to specific pages in the thesis that contain counterpoints. 🤓
— Jameson Lopp (@lopp) June 2, 2023
Nonetheless, Lowery finally posted a URL to his thesis (for the first time, after ignoring many such requests from others) as a response to my essay; you can find it here. Despite plenty of backlash that I was refusing to "put in the work" to read the source material, those who read my first critique would have noted that it was not about the time or money. Rather, I found it ideologically objectionable that a taxpayer funded academic thesis about an open system should be hidden behind a paywall.
Now that the material is publicly accessible, I sat down and read the entire thing.
Softwar
This is a beast of a thesis, clocking in at over 200,000 words across 385 pages with 222 cited references. Here's a word cloud I generated from the text:

Chapter 1: Introduction
Based on a theoretical framework developed and presented in this thesis called “Power Projection Theory,” the author hypothesizes that Bitcoin is not strictly a monetary technology, but the world’s first globally-adopted “softwar” protocol that could transform the nature of power projection in the digital age and possibly even represent a vital national strategic priority for US citizens to adopt as quickly as possible.
Lowery is correct that Bitcoin is not strictly a monetary technology. Bitcoin creates new game theory. Lowery correctly analyzes (some of) that game theory, but as we'll see, he falls short in explaining how Bitcoin's game theory can be applied practically to non-Bitcoin data.
In some places it seems Lowery suggests that we could create other Proof of Work systems. But, as Lowery is fond of quoting Michael Saylor, "there is no second best." Time and time again we have seen that with any given Proof of Work algorithm, there can only be one top dog. It's rather unclear what Lowery is advocating for specifically.
Lowery suggests many times that nations may prefer to engage in cyber power based war rather than kinetic war.
A soft form of warfighting would give people access to the supreme court of physical power, and that court would likely be just as indiscriminate and impartial in electronic form as it already is in kinetic form. For this reason, soft warfighting protocols could be ideal for small countries wielding small amounts of kinetic power (i.e. small militaries) seeking to settle policy disputes with larger countries wielding large amounts of kinetic power (i.e. big militaries).
This is an odd claim that I'd like to see further analysis upon; my intuition tells me that nations with small militaries likely have far less energy (cyber power) than nations with large militaries, so they'll likely lose either conflict.
a soft form of warfighting would represent a non-lethal form of warfighting – making it a potentially game-changing and revolutionary way for nations to establish, enforce, and secure international policy.
This is a massive claim; it seems Lowery is basically proposing that a Proof of Work system could serve as a superior replacement to international bodies like the United Nations?
Things like constitutions and rules of law have always been disembodied and immaterial, so who says they can’t be physically secured against systemic exploitation and abuse in a disembodied and immaterial way?
I wonder if we'll ever learn how to accomplish this...
Imagine if society were to discover a way to write down policies using C++ instead of parchment, then enforce and secure those policies using physically harmless electric power. A discovery like that could change society’s perception about the moral value of traditional laws and warfare simultaneously.
OK but that involves writing completely different non-Bitcoin protocols, assuming that the protocol is the policy. And it still relies more on nodes to enforce rules than proof of work. I thought this thesis was about how Bitcoin will enable the settling of such policy disputes?
It's interesting to see this omission because then Lowery would have to admit that much of Bitcoin's security model is based upon "logical security."
By converting kinetic warfighting or physical security operations into digital-electric form, written rulesets (e.g. laws) that are inherently vulnerable to systemic exploitation can be secured using (non-lethal) electric power rather than (lethal) kinetic power. International policies (e.g. monetary policy) could be written in C++ and secured using (non-lethal) electronic power rather than being written on parchment and secured using (lethal) kinetic power.
Here we start to bump into one of my major problems with Lowery's thesis. The encoding of rules / policies via programming languages such as C++ are "logical security" by Lowery's own definition. Even proof of work checks are encoded in the same fashion. And proof of work validation is tangential to the validation of all the other rules in the system.
Bitcoin could therefore represent something far more than just a new financial system architecture. Once we have figured out how to keep financial bits of information physically secure against attack, that means we have figured out how to keep all bits of information physically secure against attack.
... how? The method used by Bitcoin does NOT scale for securing large volumes of data! Herein lies another massive leap of faith. Will Lowery connect the dots?
Chapter 2: Methodology
It's fascinating that Lowery expends an entire chapter (16 pages) of the thesis expounding upon the virtues of Grounded Theory as a great way to approach novel, multi-disciplinary concepts.
One of the most commonly-cited mistakes of researchers using the grounded theory methodology is that they become too self-restrictive.
And yet this entire thesis is narrowly focused upon the Proof of Work aspect of Bitcoin's security model...
Chapter 3: Power Projection Tactics in Nature
As noted in my previous essay, this chapter is all quality material. The point is that nature exists in a state of anarchy and the only "rules" are those of physics. Thus "ownership" of "property" is ultimately a game of "might makes right" and one could consider all forms of life to be engaging in perpetual warfare over scarce resources.
That is to say: you can't truly own something unless you can defend it from threats.
Lowery manages to make this chapter more compelling by speaking of resources, and the cost and benefit of attacking to gain more resources (and defending your current resources,) in terms of watts. From a physics standpoint, this is brilliant framing because all living organisms are fundamentally fighting against entropy. Of course, just because the framing is smart doesn't mean it's a perfect description.
I grew up camping in places with black widows. Perfect example. One of those little fuckers could impose a severe physical cost on me, but did not need to expend a lot of watts to do so. A rabbit can produce several orders of magnitude more energy, but I didn't avoid the rabbit
— Rijndael (@rot13maxi) May 28, 2023
Lowery goes on discussing evolutionary biology to note that cooperation is a key survival strategy, and organizations employ the same type of strategy as single celled organisms and pack animals. Presumably the tie-in is that Bitcoin is a protocol that enables cooperation.
I did find it amusing that Lowery spends a while discussing the history of humans domesticating animals and then using that to warn that we should use it as a lesson to reject the domestication of humans (by stripping their power projection.) It's amusing because he's describing exactly what governments (his employer) do to their citizens.
Lowery then goes on to note that characteristics such as antlers enables members of a species to project power against external threats while still being able to settle their internal disputes via projection of power in a way that is less likely to have lethal consequences. This is good for pack animals that are disinclined to weaken the pack. It's clear that this is the lead-in to his framing of proof of work as "non-lethal warfare."
Chapter 4: Power Projection Tactics in Human Society
Lowery accurately notes that humans are disinclined to use physical force against each other to settle disputes; we prefer to use our communication skills to use abstract power such as courts to find non-violent solutions. Of course, all of these abstract power sources are ultimately backed by a source of physical power. And, sometimes, the abstract power fails to resolve a dispute and we fall back to kinetic warfare.
This chapter focuses on the root causes of warfare and explains why it's desirable for humanity to have non-lethal options. It's not a controversial statement to say that human infighting is the most destructive intraspecies competition on our planet.
Lowery approaches the human brain and its power for imagination and abstract thinking, citing this ability as an enabler for humans to create stories, narratives, and belief systems that enable us to bypass Dunbar's Number. That is, belief systems create scalable trust and coordination that wouldn't be possible otherwise because we're only physically capable of maintaining close relationships with about 150 other humans.
In other words, storytelling is an abstract superpower.
This line really stuck out at me given my characterization of Lowery's efforts in my previous critique:
Lowery is a gifted storyteller.
I dare say that Lowery is employing his own thesis against his audience, in multiple ways!
- Lowery has deployed a compelling story that causes many to overlook its flaws.
- He sought (until last week) to impose costs upon his critics by requiring them to buy his book on Amazon.
- He seeks to impose costs upon critics by requiring them to read a 400 page thesis before questioning any of his claims.
"With the right stories, people will forfeit their physical power or lay down their arms. Sapiens can be domesticated by the stories they believe, and like lambs, they will walk straight into slaughter."
Indeed. Beware which stories you believe...
Lowery goes on to explain that abstract power systems are exploitable through dogma and politics. Basically, the best storytellers win, attaining the position of "god-king."
I have very few objections with the content in this chapter; here's a particularly powerful point with which I fully agree:
If our Upper Paleolithic ancestors could see how modern agrarian domesticated sapiens live today, they would probably not envy our lives. Humans replaced the emotionally fulfilling challenge of hunting and gathering with unnaturally sedentary and laborious lives filled with social isolation, infectious diseases, health deficiencies, warfighting, and probably most devastating of all, high-ranking sociopaths who psychologically abuse and systemically exploit their populations through their belief systems at extraordinary scale.
Here's a truism I've found is applicable to many aspects of civilization.
When sapiens trade physical power for abstract power, they make a tradeoff in complex emergent behavior. What they sacrifice in the trade is systemic security.
I believe this statement can also be modified to replace "physical power" with "responsibility" and "abstract power" with "convenience." That is to say: civilization advances via specialization of work; specialization enables greater efficiency. But over many generations, humans outsource more and more aspects of their lives to third party specialists... and today we live in a society where very few humans are actually capable of surviving without a massive network of trusted third parties. This creates a huge systemic risk.
It's therefore entirely possible that a direct contributing factor of warfare is, counterintuitively, the abstract power hierarchies we ostensibly use to avoid warfare.
Indeed, conflict and warfare seem unavoidable. Perhaps our structure of modern civilization means that wars are less common, but of much greater severity when they do occur.
Consider a Roman-style senate of 100 high-ranking people wielding control authority over a population in the form of voting power. All it takes to achieve unimpeachable control over the entire population is for 51 of those high-ranking people to collaborate as a centralized entity.
I do find it interesting that Lowery cites this example as being a point of weakness with "abstract power" (and later makes a similar point about Congress) and yet he never addresses the issue of 51% attacks in Proof of Work...
Warfare is the reason why control over our valuable resources remains decentralized.
I suppose this could be an implicit counter to objections about 51% attacks. But, if so, I'd point out that Bitcoin's hashpower is already guaranteed to be highly decentralized. It doesn't need nation states to ensure its decentralization - the very nature of energy itself ensures that. That, and the game theory that incentivizes miners. As mentioned in my previous essay, nationalization of mining could disrupt that game theory...
I do like that Lowery brings up a counterpoint to the folks who dislike discussions about "violence" and "warfare."
The solution? Simply don’t call it warfare. Call it something else like primordial economics.
At last we do get to a scenario that makes sense for why some nations would prefer to engage in cyberwarfare rather than kinetic warfare: nuclear power states are unable to directly engage in physical combat because they know it will ultimately end in a stalemate due to mutually assured destruction. But of course, this does not apply to non-nuclear nations.
Chapter 5: Power Projection Tactics in Cyberspace
This chapter links together key concepts in computer theory and cyber security that are needed to understand why software is fundamentally a belief system which gives a select few people abstract power.
Oh boy. Lowery makes the point that software companies have attained the position of "god-kings" who project power through cyberspace by building their own belief systems. Not entirely wrong, though I'd counter that it doesn't really apply to volunteer-driven open source projects. The real problem is the centralization of much of the world's information and communication into the hands of a few organizations.
Here comes the big claim...
... bits of information secured on the Bitcoin network could denote any type of information, not exclusively financial information. Instead, Bitcoin could represent a completely new system for securing any information in cyberspace – a way to keep bits of information secure against belligerent actors by physically constraining them, not logically constraining them.
This is where the thesis starts to get weird. Lowery spends the next 8 pages describing how computers (finite state machines) operate, with his goal being to convince the reader that software and the computations performed by hardware running software "are not real." Thus he casts software developers as "storytellers" who wield god-king power similar to that of politicians.
Everything printed on the screen of a general-purpose computer is a computer-generated illusion. Whether it be a line of text, or a detailed image, or an imaginary object, or a three-dimensional interactive environment that looks and behaves just like environments experienced in shared objective reality, what a machine shows on a screen is virtual reality. Virtual reality is, by definition, not physically real. The only knowledge a person can gain from looking at a computer screen is symbolic knowledge, not experiential knowledge. This is true even if what’s shown on screen is an image of something real or an event which did physically happen.
His point being that:
Software is nothing but a belief system, and belief systems are vulnerable to exploitation and abuse, particularly by those who pull the strings of our computers.
Software is a system of encoded rules. Much like any system of rules, what matter is the "governance" - how those rules get changed. Lowery goes on to discuss various cybersecurity principles, noting that software always operates as it is instructed. According to Lowery, his most important point other than proof of work cost imposition protocols is that:
Because software doesn’t physically exist, it’s not possible to secure software using physical constraints unless the underlying state mechanism is physically constrained.
As noted in my previous essay, this claim is nonsensical to me. There are a variety of best practices available to secure software against tampering; many of these mechanisms use cryptography. By relying upon cryptography we can pull issues of "encoded logic" into the physical realm by turning the digital security problem into a physical (private key management) security problem.
Lowery continues for the next dozen pages expounding upon why it's difficult to engineer secure software, and lamenting upon the fact that most software developers are not security experts and probably not even computer science majors. OK, sure, there's basically no such thing as perfectly secure software. Not even highly scrutinized Bitcoin software...
Now it's going a bit off the rails...
Herein lies one of the most significant but unspoken security flaws of modern software: it creates a new type of oppressive empire. A technocratic ruling class of computer programmers can gain control authority over billions of people’s computers, giving them the capacity to exploit populations at unprecedented scale. These digital-age “god-kings” are exploiting people’s belief systems through software, data mining people and running constant experiments on entire populations to learn how to network target them to influence their decisions and steer their behavior.
I can't wait to hear how Proof of Work solves this! Lowery continues to explain that software engineers are building entirely new realities in cyberspace, analogous to early versions of The Matrix. He suggests that the only way to save users from malicious software and untrustworthy system administrators is to rearchitect the internet itself.
In 5.7.3 Lowery notes that US military personnel physically secure their encryption keys by carrying them on specially-designed common access cards, so it turns out he does understand the concept of pulling digital security into the physical realm.
it is theoretically possible to create computer programs that are inherently secure because it’s either physically impossible or too physically difficult to put them into a hazardous state, simply by intentionally applying physical constraints to the underlying state mechanisms running the software. It is also theoretically possible to design computer protocols which can apply real-world physical constraints to other people’s computer programs in, from, and through cyberspace. The protocol is called proof-of-work.
This one's a head scratcher. I suspect nearly all security experts would scoff at the claim that a computer program can be "inherently secure." One fundamental issue immediately leaps to mind: Lowery claims that software itself can be secured through proof of work. But what is going to be checking the proof of work? If you guessed "software" then you're correct! My perspective is that if Lowery can hand-wave away other security mechanisms based upon cryptography as "encoded logic" then how is checking a proof of work not also "encoded logic" that can be similarly manipulated? Also, any such software will by definition need to be written and maintained by the very developers Lowery has spent dozens of pages warning us about. It's turtles all the way down, folks.
Lowery then describes a "proof of power" wallet concept that's basically hashcash. I implemented this exact concept on my web site:
Email spam, comment spam, sybil attacks, bots, troll farms, and weaponized misinformation stem from the exact same types of core design flaws which proof-of-power wall APIs could theoretically help to alleviate.
I think "alleviate" is a key word here. Proof of work imposes a cost, yes, but it does not stop all unwanted control signals. I still receive unwanted messages through my web site, just far fewer than if I didn't require any proof of work. On the flip side, it can be a pretty crappy user experience if you have to wait tens of seconds or even minutes between being able to perform actions like leaving a comment. This is due to the poisson distribution of clock time that it takes for a computer to solve any given proof of work request.
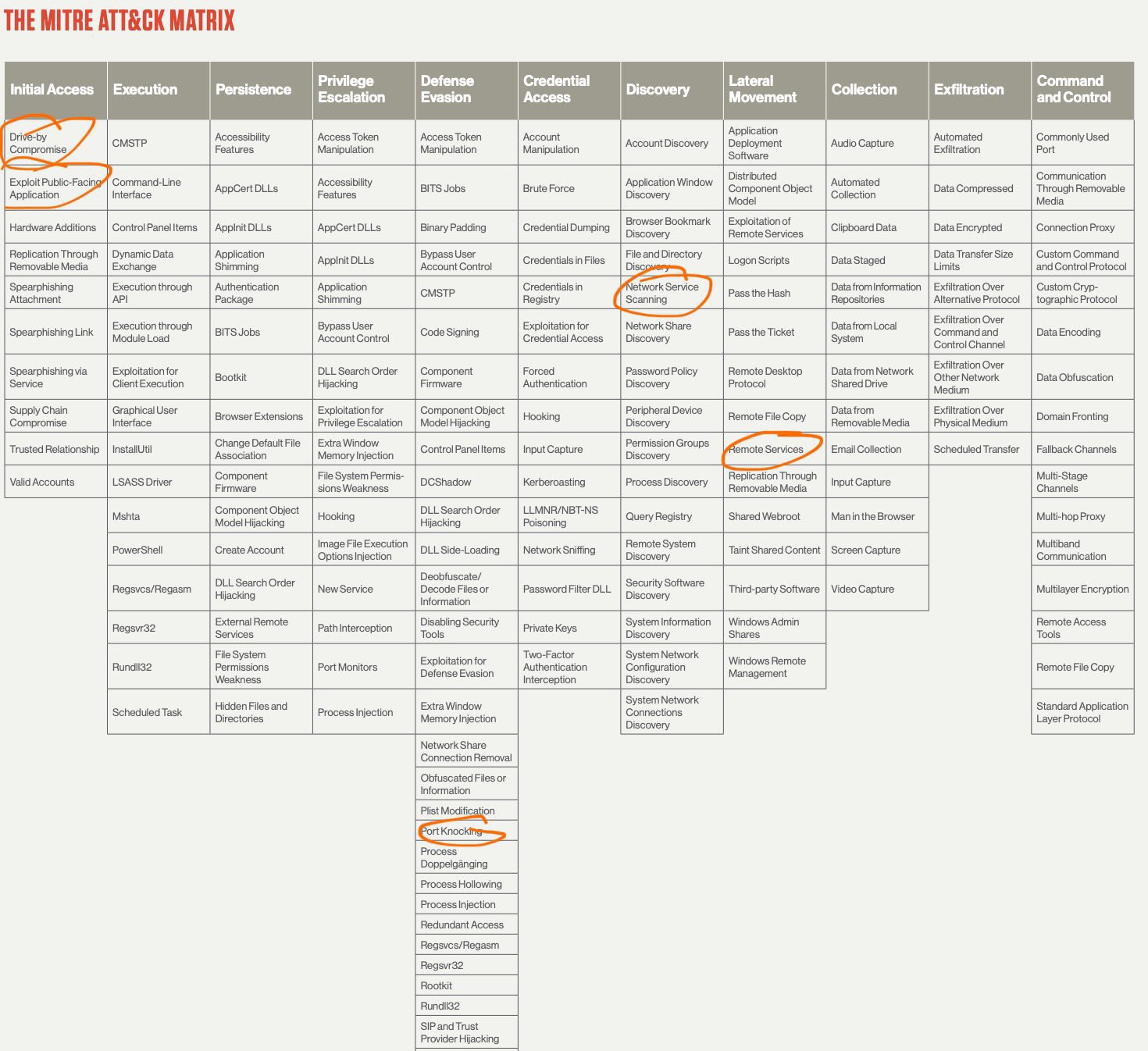
To further understand why a "proof of power wall" is not a security panacea, it would only help alleviate a small fraction of attack vectors:
By using its own proof-of-power electro-cyber dome design concept to secure itself, Bitcoin has managed to remain operational for thirteen years without being systemically exploited (i.e. hacked). It is not that people don’t know how to exploit/hack Bitcoin’s ledger, it’s that it’s impossible for attackers to either justify or overcome the immense physical cost (a.k.a. watts) of exploiting Bitcoin’s ledger because it’s parked behind an electro-cyber dome.
This is simply incorrect. Bitcoin has been exploited at the protocol level before (in 2010) and has had similarly bad vulnerabilities patched (thankfully) before they were exploited. Bitcoin's proof of work rules didn't protect it from any of those vulnerabilities. Proof of work is not a security panacea.
It’s theoretically possible that Bitcoin could be emerging as the base-layer operating system for a planetary-scale computer.
Ahuh; so perhaps we're getting closer to an explanation of how Bitcoin fixes the entire field of cybersecurity?
Not only would it be possible to utilize the planet itself as a large, heavy, slow, and energy-intensive computer, the infrastructure and circuitry required to accomplish this has already been built – we call it the global electronic power grid. Herein lies a simple, but profound idea: to create the world’s largest, heaviest, most energy-intensive, and most physically-difficult-to-operate computer ever built, we could simply utilize our planet’s energy resources as the controllable physical-state-changing mechanism of a planetary-scale computer, where the globally-distributed electronic power grid serves as its circuit board.
This sounds like the "macrochip" concept Lowery has tried to explain on a few podcasts. This metaphor makes no sense to me, as the electrical grid does not act like a circuit board of a computer with regard to Bitcoin mining. All of the electricity consumed for Bitcoin mining happens independently; it doesn't flow toward a specific area to aid in computing anything. If anything, the power grid just acts as the power supply to Bitcoin's state change mechanism.
A planetary-scale computer like this could theoretically create a portion of the internet where no single person or organization has full control over it, thus they have no ability to fully control the bits of information transferred, received, and stored on it. This decentralized portion of the internet could be reverse-optimized to be more expensive and energy-intensive to send, receive, and store every bit, giving it complex emergent behavior that no other computer connected to the internet would be physically capable of replicating.
So what is Lowery actually proposing? It sounds like he wants Ethereum (or a turing complete system,) but powered by proof of work? Bitcoin is a poor substitute for a general purpose computer because its progammability is extremely limited (by design) and its throughput is extremely limited (by design.) Lowery has done a good job explaining WHY such a machine is desirable. But the HOW is a gaping hole of questions.
It would theoretically be possible to utilize an open-source, internet-accessible, planetary-scale computer to perform these functions. The key to doing this effectively would be finding a way to “chain down” or couple ordinary state mechanisms to this new planetary-scale state mechanism.
Right. All we need to do is figure out how to do it...
By applying Boolean logic to the power grid, people convert large and expensive quantities of physical power into bits of information and feed that information back into our regular computers via the internet. People then use that information to affect state changes inside their ordinary computers. The result of this activity is a capability which does not appear to have existed before: the ability to impose severe physical costs and thermodynamic constraints on people, programs, and computer programmers operating in, from, and through cyberspace in a zero-trust, egalitarian, and permissionless way that no person or organization can fully control.
Aside from the overly repetitive and verbose descriptions of how Bitcoin operates, there's something else bugging me here. Bitcoin does not actually impose a thermodynamic cost upon all users to activate state changes to the ledger. Anyone can do that by paying a relatively small transaction fee. Also, as mentioned in my previous essay, there are many mechanisms that prevent invalid state change requests from ever even reaching miners - rules enforced by fully validating nodes. Once again we see that Lowery's focus on Proof of Work seems to have put blinders on him with regard to how all the other pieces of the system work.
Proof-of-power signals produced by physical cost function protocols like Bitcoin could theoretically double as proof-of-real signals, to serve the same function as kinetic power (i.e. poking/pinching). At the same time, proof-of-power could also be used to legitimize or delegitimize computer programmers who otherwise have unrestricted abstract power and control over the illusions we see in cyberspace.
This is a huge stretch. Even after reading 300 pages and generally agreeing with the premises presented, I don't see how imposing non-trivial costs on state changes makes them more real. All it does is ensure that the state changes are by definition more economically valuable to the entity that is making them.
As of now, these ideas are nothing more than theories grounded by the author’s first principles approach to exploring the benefits of proof-of-power (a.k.a. proof-of-work) protocols.
And there it is. We should not expect to see the dots connected between the "why" and the "how" of this thesis.
Chapter 6: Recommendations
The author challenges computer scientists and software engineers to take inventory of their assumptions and ask themselves, “what could be the value of having increasingly more physically restricted command actions and bits of information in the global cyber domain?”
Fair. This is what blew my mind when I first read the Bitcoin whitepaper - it solved the Byzantine Generals Problem in the exact opposite way of what I would have expected based upon my computer science education.
With the global adoption of cyberspace combined with the global adoption of an electro-cyber form of physical power competition enabled by proof-of-work technologies like Bitcoin, humanity could be at the dawn of creating a completely new type of polity that it has never seen before – a new or adjusted type of governance system which enables the formation of an organized society that resembles something on par with (or perhaps even superior to) a traditional government.
Perhaps, though I'd say this is far from conclusive. I do agree that Bitcoin has inverted the traditional structure of governance; I gave a keynote about it in 2018. It's clear that we can create novel cyber governance structures with this technology, but I'm unconvinced that meatspace governance can be performed in the same manner.
Stop Relying Exclusively on Financial, Monetary, and Economic Theorists to Influence Bitcoin Policy
Sure; everyone has their own (narrow) take on Bitcoin which leads to blind spots. Somewhat amusingly, Softwar is no exception given its focus on Proof of Work while ignoring many other dynamics of Bitcoin's governance and security model.
Think of Bitcoin as an Electro-Cyber Security System rather than a Monetary System
Sure; I've always said that Bitcoin is far more than just money. It's an authoritative historical record that is programmable (to an extent.)
Consider the Idea of Protecting Bitcoin under the Second Amendment of the US Constitution
As mentioned in my previous essay, I find this to be a weak idea, but I'll leave that to the lawyers to muse upon.
Recognize that Proof-of-Stake is not a Viable Replacement for Proof-of-Work
Absolutely; stake is not a novel system, it's just a digital version of traditional abstract power.
If we Make the Mistake of Expecting the Next World War to Look Like the Last World War, we could Lose it before we Realize that it has Already Started
Sure. The only constant is change.
Conclusion
The first four chapters of Softwar are an informative and entertaining perspective of military history and evolutionary biology. This paper works well as an anthropological thesis about human governance.
Warfare creates an existential imperative for people to adopt increasingly larger (and thus more dysfunctional and vulnerable to systemic exploitation) abstract power hierarchies which create increasingly larger security hazards capable of leading to increasingly larger losses. Dysfunctional abstract power hierarchies motivate people to wage wars, which are won by adopting larger-scale abstract power hierarchies (e.g. national power alliances) to scale cooperation and sum enough physical power together to win the war. This creates a cyclical, self-perpetuating process where civilization learns to cooperate at higher scales, but also learns to fight at increasingly larger and more destructive scales, driving them to adopt increasingly more systemically insecure and hazardous belief systems.
However, Softwar falls short on acting as a blueprint for how we should build the future. In some cases Lowery broadly refers to "bitpower protocols" as being the solution to these problems, in other cases he says Bitcoin is the solution.
Additionally, he never addresses the "garbage in, garbage out" problem inherent to all databases. He likes to frame bitpower as creating "objectivity / truth / realness" with regard to control actions, but I find that to be a mischaracterization of what imposing economic cost actually does.
I think Lowery made a huge blunder by failing to ever mention the dynamics of how Bitcoin's own "civil war" played out. By expending all of his resources focused on many millennia of animal and human evolution he failed to learn from a directly applicable piece of recent history.
I'll also note that NONE of the issues I pointed out in my first essay were addressed in the full thesis. Clearly the "you haven't read the thesis" argument was a deflection. I will once again invite anyone who cares to make specific counterpoints to my critiques rather than attempting to dismiss me outright.
Finally, I think the narrow focus on a single facet of Bitcoin's security model is what leads to so many errors of omission in this thesis. Just to put it in perspective, here are some counts of how many times these words appear:
- watt: 149
- severe physical costs: 114
- hash*: 61
- game theory: 5
- governance: 2
- node: 2
- open source: 1
I can sum up my disappointment in Lowery's narrow focus on hashpower with a fairly old retort I gave to big blockers who were spewing "might makes right" arguments about miners determining the protocol rules back during the scaling debates.
It takes ~40,000 kilowatt-hours to mint a block, yet this power can't overcome a few lines of code being run on a 4 watt Raspberry Pi.
— Jameson Lopp (@lopp) April 15, 2017