Casa's Privacy Model
At Casa our goal is to make it easy for non-technical crypto asset owners to be their own bank. While we have no intention of providing custodial services to our users, we do wish to provide financial software and services that help facilitate our users in their quest for financial sovereignty. As such, there will be some data that third parties such as Casa may know about your crypto activity. We keep as much of your data private as possible, but here is some detail on what third parties will see and your options for taking steps to strengthen your privacy if you so desire.

App Ecosystem Privacy
The entity that owns the app store (Apple or Google) will know that you have the app installed, as will your mobile phone service provider; these entities may also collect some statistics around your use of it. If you want the ultimate level of privacy, then you’d need to create a new AppleID / Google account that isn’t connected to your identity, buy a smart phone with cash and either buy a no-contract prepaid phone plan or limit yourself to only using the phone via wifi.
Internet Privacy
Your ISP will also know that you are using Casa, though they won’t know exactly what you’re doing. Traffic between your device and Casa is encrypted, but they know that requests are going to Casa’s servers. If you want to improve this aspect of your network privacy then you’ll want to use a VPN on your phone and other devices that you use to interface with Casa. This way your ISP only knows that you’re sending traffic to a VPN server. This isn’t perfect privacy though, because you’re still trusting a third party (the VPN service) to not spy on your activity. If you wanted to take it a step further then you’ll want to configure Tor clients on any device that you use to interface with Casa.
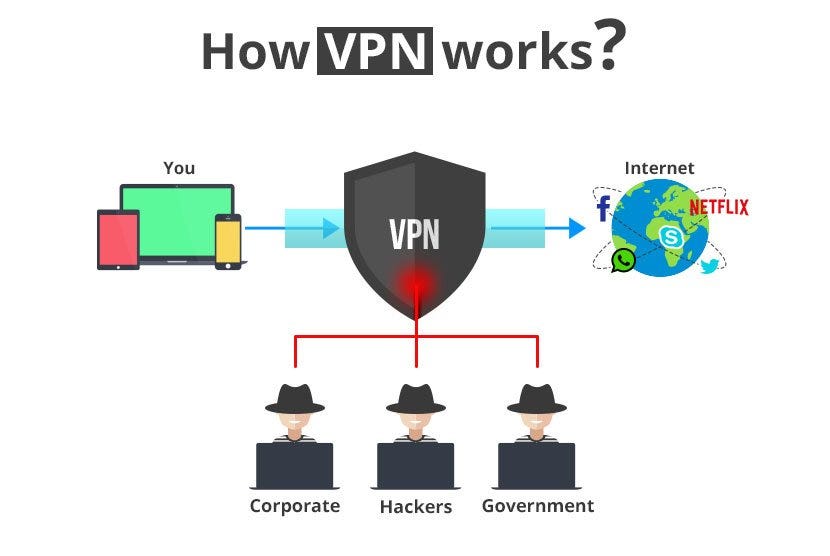
Another reason you may wish to use a VPN or Tor is due to logging. Casa has no intention of logging IP addresses of clients who connect to our servers, but if you want to be 100% certain that your IP address never ends up in any logs then it’s best to use a proxy of some sort. Also, because we use Cloudflare, it’s possible that your IP address will be logged by them — we have no control over their logging. By not connecting from your real IP address, this becomes a non-issue.
Crypto Asset Network Privacy
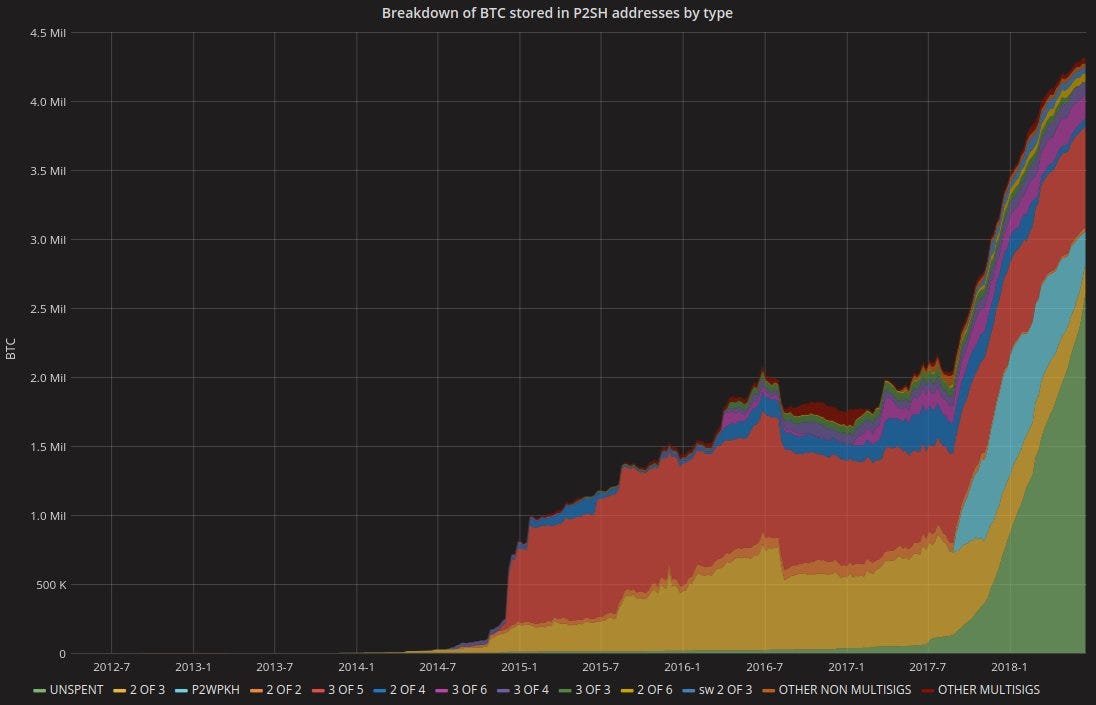
Blockchain observers will be able to tell that you’re spending from a 3-of-5 multisig wallet. As we can see here, 3-of-5 is a pretty popular multi-sig scheme in terms of total value stored, but the number of distinct UTXOs is not particularly high and thus it considerably narrows down the potential set of wallets from which an attacker may try to guess is yours.
Network observers may be able to determine that transactions are being broadcast from Casa’s nodes. One potential improvement Casa can make here would be to only broadcast via Tor; eventually Dandelion should mitigate this concern by making it quite difficult for network observers to deduce the origin of a transaction simply by which peers announced it first.
If an attacker compromises Casa’s servers, they can obtain additional information, though they can’t steal your funds. In terms of personally identifiable information we store a name and email address, but you are welcome to use a pseudonym. Casa also stores your extended public keys, which an attacker could use to determine all of the addresses and transactions that belong to your wallet — but not spend your funds. This is a tradeoff we made due to the vast improvements in usability we can provide by storing your public addresses. It’s also worth noting that an attacker who gained full control of this database could theoretically change these xpubs and addresses in an attempt to fool users into depositing assets into the wrong wallet, but we have mitigations in place to significantly hinder this, and we’re making improvements which will remove it as an attack vector entirely. More details on that in a future post.
Physical Address Privacy
As a convenience to our customers who may need to replace hardware key management devices from time to time, Casa will provide the option of sending them directly, which requires giving us a shipping address. We have no interest in knowing the physical addresses of our users, so we recommend having devices either shipped to a private mailbox, PO Box, or if you’re in the US you may elect to use the USPS “Hold for Pickup” option where you can just have deliveries sent to a USPS office that you select. The recipient will have to show a government issued ID to get the package — but this at least eliminates the need for Casa to know your home address.
Real World Identity Privacy
One of Casa’s offerings is a key recovery service — if you lose multiple devices (sets of keys) to your vault then we have the ability to help recover your funds and help you set up a new vault. The trade-off to this convenience is that Casa must have a way to verify the identity of the person who is making a recovery request. While we are not going the AML / KYC route and requiring government issued identification documents, we have alternative means of authentication such as recovery questions and photos. Any recovery data is stored encrypted in our database and can only be decrypted by select security officers. We only use this information to determine if it's the real account owner who is requesting to make changes to an account such as resetting a password or performing a Casa-facilitated key recovery. While some users may which to take a selfie for their recovery photo, it's also acceptable to take a photo of some other object that you essentially use as a 2FA secret.
Maintaining Privacy is Hard
We expect that most Casa users will value the security we offer (more on that in another post) more heavily than the privacy attributes. The simple truth is that if you want perfect privacy you can’t be interacting with third parties — you have to act as a lone wolf. The downside is that this creates a much steeper learning curve that you must climb in order to duplicate all of the services being offered by a more complex organization. Casa can’t offer perfect privacy, but we will strive to offer an optimal set of trade-offs to balance usability, privacy, and security for our clients.